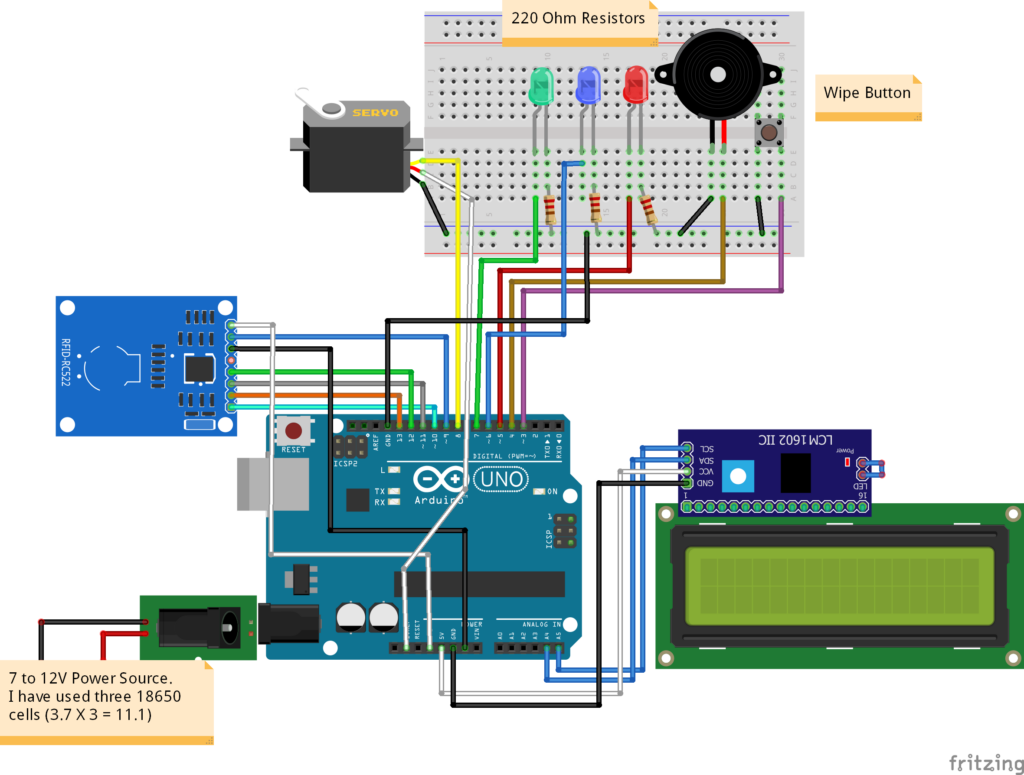
How to Set Up an RFID-Based Access Control System
RFID technology has revolutionized access control systems by providing a convenient and secure way to manage who can access certain areas. If you’re considering implementing an RFID-based access control system for your business or organization, this guide will walk you through the steps needed to set it up effectively.
Step 1: Choose the Right RFID Readers
The first step in setting up an RFID-based access control system is choosing the right RFID readers. There are several types of RFID readers available, including proximity readers, smart card readers, and biometric readers. Consider the specific needs of your organization to determine which type of reader will work best for you.
Step 2: Install Access Control Software
Once you have selected the RFID readers, the next step is to install access control software. This software will allow you to configure the system, manage user permissions, and track access events. Make sure to choose a reputable software provider that offers regular updates and technical support.
Step 3: Enroll Users and Assign Credentials
After installing the access control software, you will need to enroll users and assign them RFID credentials. This can typically be done through the software interface, where you can input user information and assign access levels. Be sure to provide proper training to users on how to use their RFID credentials.
Step 4: Configure Access Rules and Permissions
Once users are enrolled, you can configure access rules and permissions within the software. This includes setting up restricted areas, defining access schedules, and creating rules for automatic door locks. Make sure to test the access rules thoroughly to ensure they work as intended.
Step 5: Test the System
Before fully implementing the RFID-based access control system, it is important to thoroughly test the system to identify any potential issues or vulnerabilities. Test the system with different users, verify that access rules are enforced correctly, and ensure that the system integrates seamlessly with your existing security infrastructure.
Step 6: Train Users and Admins
Once the system has been tested and is ready for deployment, provide comprehensive training to users and administrators on how to use the system effectively. Make sure to cover topics such as badge placement, door entry procedures, and troubleshooting common issues. Regular refresher training sessions may also be necessary.
Step 7: Monitor and Maintain the System
After the RFID-based access control system is up and running, it is crucial to monitor and maintain the system regularly. This includes regularly updating software, monitoring access logs for any unusual activity, and conducting routine maintenance of the hardware components. By staying proactive, you can ensure the long-term success of your access control system.
Setting up an RFID-based access control system requires careful planning, proper installation, and ongoing maintenance. By following these steps and best practices, you can implement a secure and efficient access control system that meets the unique needs of your organization.
How to Set Up an RFID-Based Access Control System
RFID technology has revolutionized access control systems by providing a convenient and secure way to manage who can access certain areas. If you’re considering implementing an RFID-based access control system for your business or organization, this guide will walk you through the steps needed to set it up effectively.
Step 1: Choose the Right RFID Readers
The first step in setting up an RFID-based access control system is choosing the right RFID readers. There are several types of RFID readers available, including proximity readers, smart card readers, and biometric readers. Consider the specific needs of your organization to determine which type of reader will work best for you.
Step 2: Install Access Control Software
Once you have selected the RFID readers, the next step is to install access control software. This software will allow you to configure the system, manage user permissions, and track access events. Make sure to choose a reputable software provider that offers regular updates and technical support.
Step 3: Enroll Users and Assign Credentials
After installing the access control software, you will need to enroll users and assign them RFID credentials. This can typically be done through the software interface, where you can input user information and assign access levels. Be sure to provide proper training to users on how to use their RFID credentials.
Step 4: Configure Access Rules and Permissions
Once users are enrolled, you can configure access rules and permissions within the software. This includes setting up restricted areas, defining access schedules, and creating rules for automatic door locks. Make sure to test the access rules thoroughly to ensure they work as intended.
Step 5: Test the System
Before fully implementing the RFID-based access control system, it is important to thoroughly test the system to identify any potential issues or vulnerabilities. Test the system with different users, verify that access rules are enforced correctly, and ensure that the system integrates seamlessly with your existing security infrastructure.
Step 6: Train Users and Admins
Once the system has been tested and is ready for deployment, provide comprehensive training to users and administrators on how to use the system effectively. Make sure to cover topics such as badge placement, door entry procedures, and troubleshooting common issues. Regular refresher training sessions may also be necessary.
Step 7: Monitor and Maintain the System
After the RFID-based access control system is up and running, it is crucial to monitor and maintain the system regularly. This includes regularly updating software, monitoring access logs for any unusual activity, and conducting routine maintenance of the hardware components. By staying proactive, you can ensure the long-term success of your access control system.
Setting up an RFID-based access control system requires careful planning, proper installation, and ongoing maintenance. By following these steps and best practices, you can implement a secure and efficient access control system that meets the unique needs of your organization.